Provisioning users with CyberArk Identity (Idaptiv)
You can use CyberArk Identity as an IdP to provision users into Clumio directly from your Active Directory (AD) Groups.
Prerequisites
- Active Directory must be connected.
- The individual setting up must have Super Admin access to Clumio and CyberArk Identity.
- The individual must be a part of a group that gets Super Admin access within Clumio.
Setup
- Ensure that your AD is connected to CyberArk Identity and that you are passing the user's first name, email, and name of all groups that the user is a part of to CyberArk Identity.
For information on how to add Azure AD to CyberArk Identity, please see this article from CyberArk Identity documentation. - Log in to the CyberArk Identity admin portal and navigate to WebApps> Clumio SAML App > SAML Response setting page
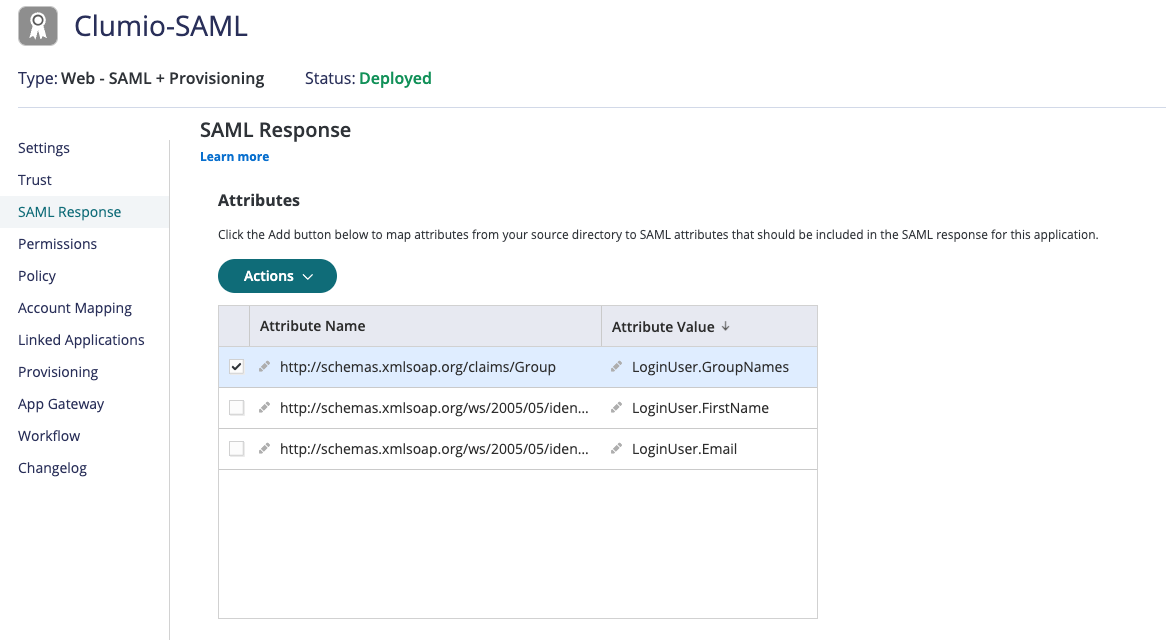
- Click on the "Add" attribute
- Add 'http://schemas.xmlsoap.org/ws/2005/05/identity/claims/name' to map to 'LoginUser.FirstName'
- Add 'http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress' to map to 'LoginUser.Email'
- Add 'https://schemas.xmlsoap.org/claims/Group' to map to 'LoginUser.GroupNames'
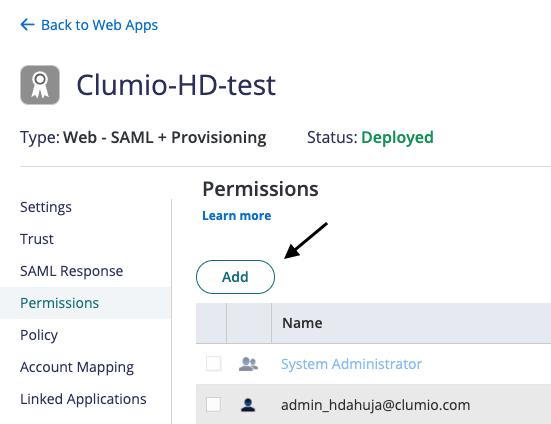
- Assign the app to the groups by navigating to the Permissions tab and adding the group.
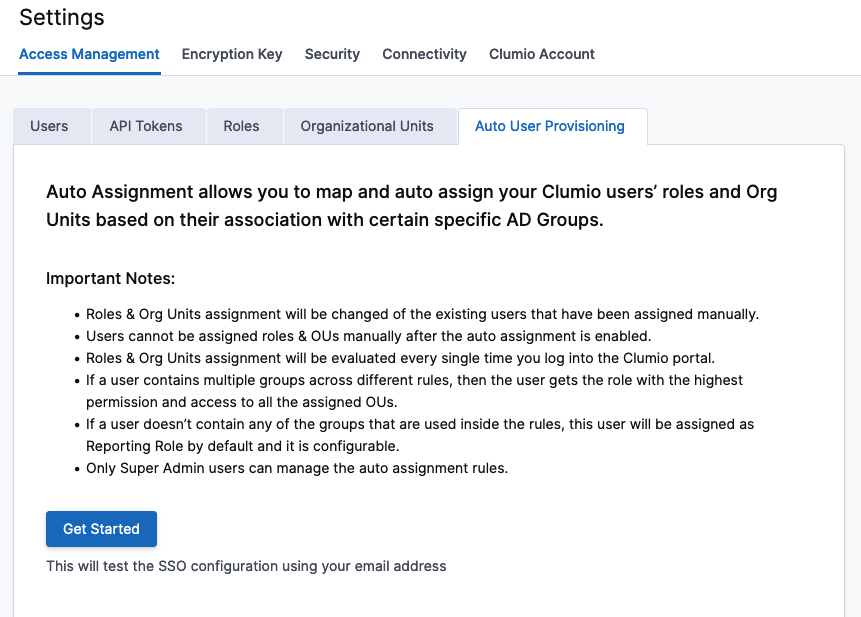
- Next, log on to the Clumio portal and navigate to Settings > Access Management > Auto user provisioning.
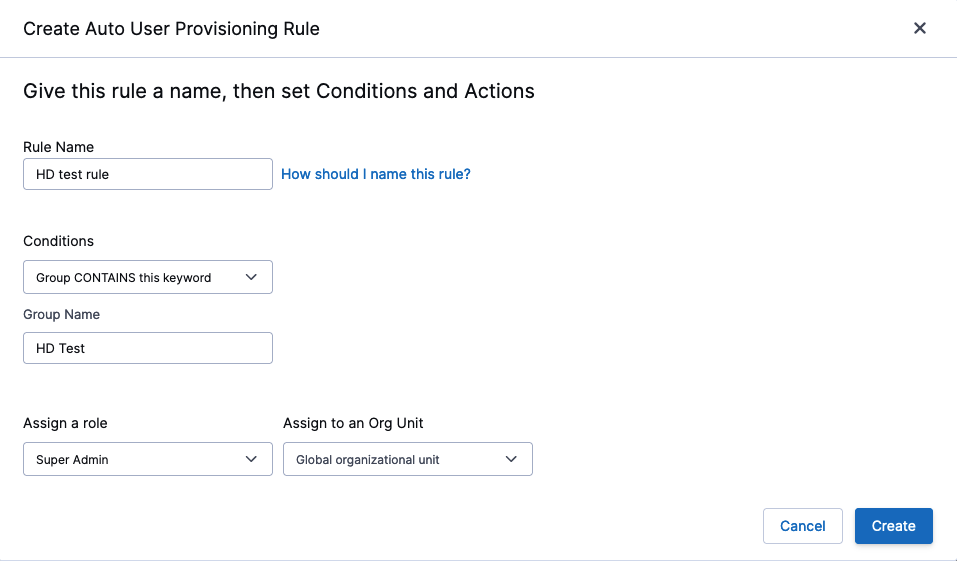
- Click Get Started and type a rule name, select the conditions to apply the rule, give the group a name, select the Super Admin Role, and assign that role to an OU (Global OU for Super Admin)
- Ensure that the logged-in user is a part of the group that is assigned the Super Admin role.
- Once the first rule has been created, click Enable Auto User Provisioning.
- You can now create additional rules per your requirements by clicking the Create Auto User Provisioning Rule button.
Once Auto User Provisioning is enabled, all users are evaluated per the rules you created.
Contact [email protected] with any questions or concerns.
Updated over 1 year ago