Parsing CloudTrail logs to check CMK activities
CMK access can be viewed in the CloudTrail in a customer's AWS account by tracking the Clumio KMS activities with the following usernames:
- 'KMS-backup' - Used during the Backup operations
- 'KMS-post-processing' - Used during the Post-processing work (FLI) operations
- 'KMS-restore' -Used during the Restore operations
- 'daebaksrv-S3Backup' - Used specifically during S3 backup operations
Any operations performed on the Clumio CMK apart from the above usernames should be reported and analyzed thoroughly by your security team.
- Log into your AWS account where the KMS key is hosted for encrypting backups stored in Clumio.
- Navigate to the CloudTrail service.
- From the left navigation pane of the CloudTrail service, select the 'Event History' tab to check the CloudTrail events.
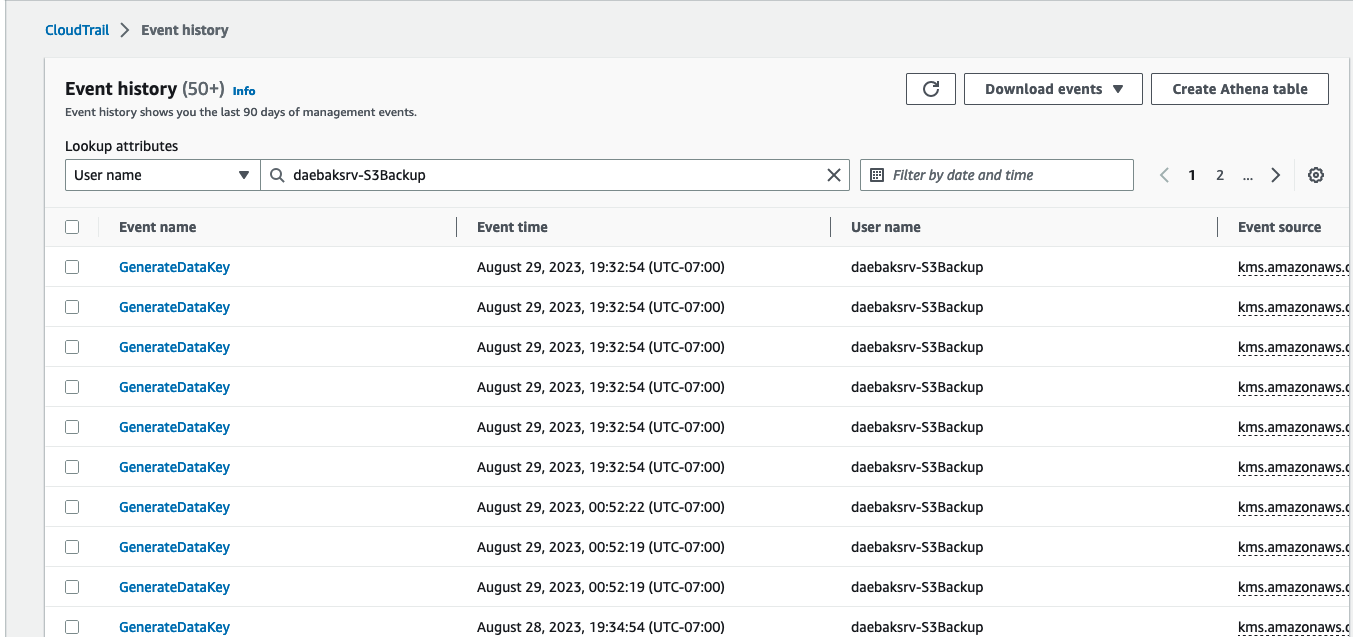
- Filter the Event History lookup attributes with the User Name attribute.
- Choose one of the User Name shared above to capture the CMK activities performed by Clumio on the shared KMS key.
Contact [email protected] with any questions.
Updated over 1 year ago