Configuring SSO for Azure
The Clumio service can integrate with Azure for seamless user authentication. Please follow the below steps to configure Azure IdP as a Single Sign On service for Clumio.
Prerequisites
Ensure that you have the following before you start configuring Azure:
- Azure account with admin privileges
- Clumio account with Super Admin Role
Enable Azure Integration with Clumio
In Azure
- Log on to your Azure portal and click on Azure Active Directory.
- Navigate to Enterprise Applications from the left-hand side tabs.
- Click +New application at the top.
- Click +Create your own application at the top.
- Provide a name for your application and click Create.
- Click Set up Single Sign-on.
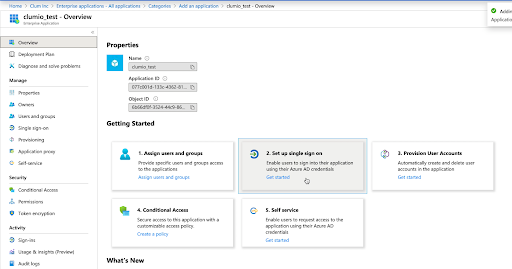
- Select SAML
- Under Basic SAML Configuration click Edit.
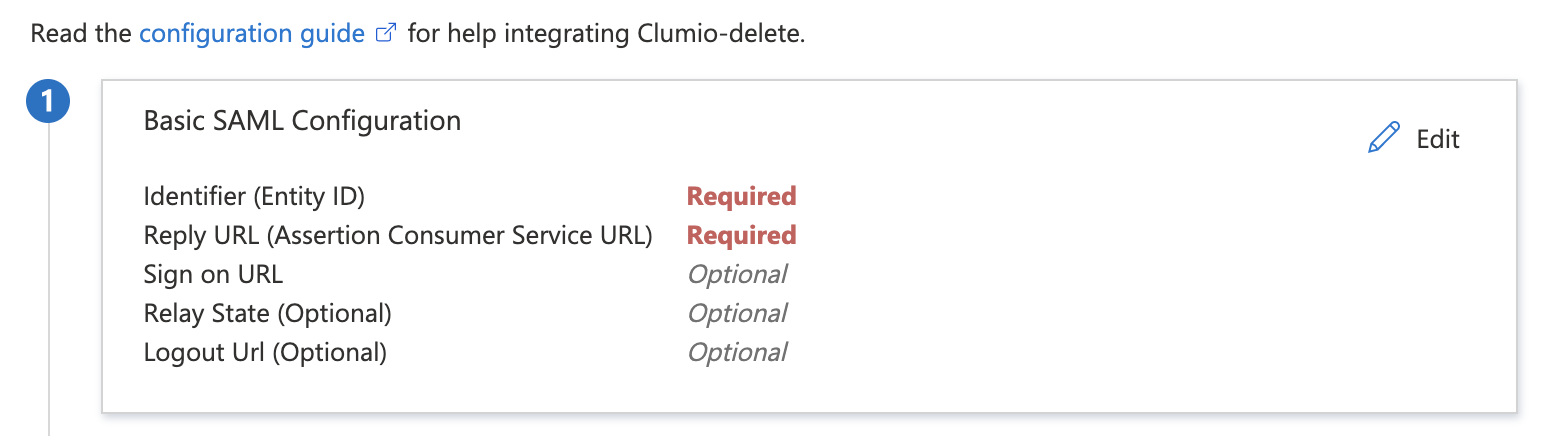
- Get the following details from Clumio (see step 4 In Clumio Section ).
- Audience Restriction
- Reply URL 1 (Assertion Customer Service (ACS) URL)
- Reply URL 2 (Default Reply URL)
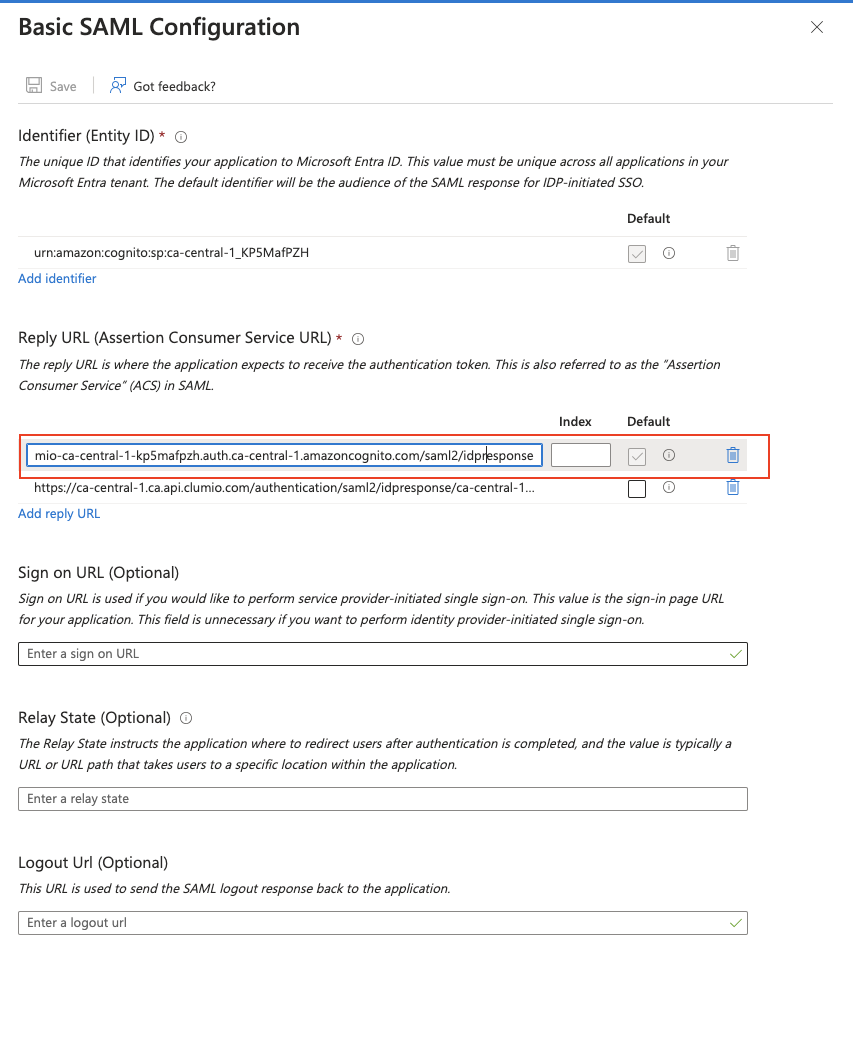
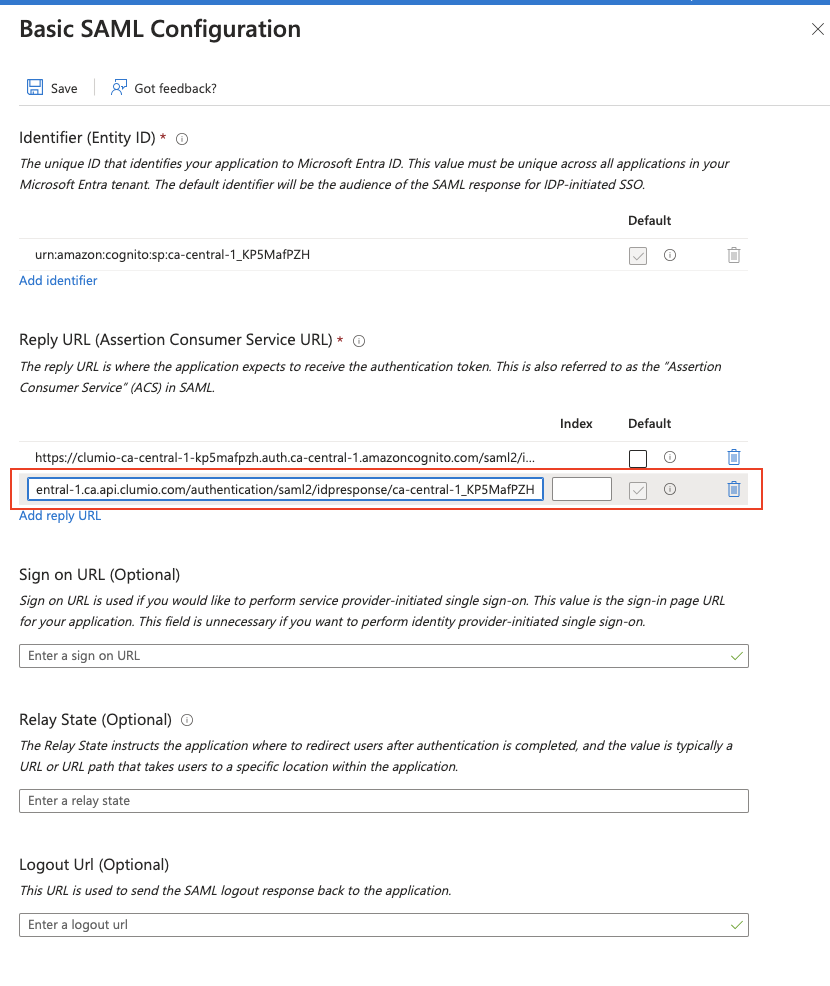
- Under Basic SAML Configuration paste the Reply URL 1 (ACS) , and Reply URL 2 obtained from the Clumio dashboard, as shown below. Click Save. Ensure that the ACS URL ending in /idpresponse is selected as the default.
- After you save the configuration, close the Basic SAML Configuration section. Navigate to the SAML Signing Certificate section and copy the App Federation Metadata Url field OR download the Federation Metadata XML. This will be needed in Clumio.
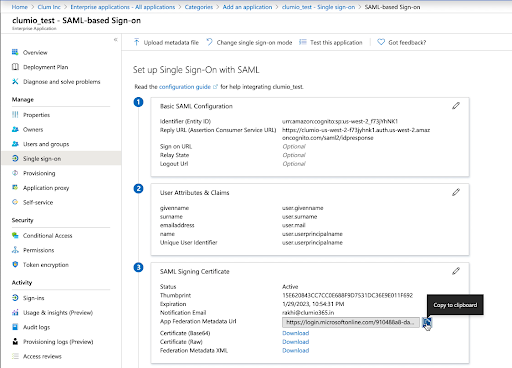
- Click Edit under the User Attributes and Claims section.
- Ensure that the Required Claim maps to Email Address and the value is either user.mail or user.userprincipalname based on your organization's use.
- Click Save.
- Once SSO has been activated, go back to Basic SAML Configuration and change the other ACS URL not ending in /idpresponse as the default and click Save.
This will make sure that both IdP initiated and SP initiated logins go through successfully.
In Clumio
- Log on to Clumio.
- Navigate to Administration > Access management > Authentication (SSO/MFA).
- Click Configure SSO.
- Select Identity provider (IdP) name as Azure
- Copy the Audience Restriction, Reply URL 1 (Assertion Customer Service (ACS) URL), and the Reply URL 2 (Default Reply URL). This will be needed for the IdP side setup.
- Scroll down and upload the metadata retrieved from the IdP. You can either use the URL, upload the metadata XML file, or configure it manually.
- Next click Save Configuration.
- Click Test with my Account. This opens a new tab to test the SSO connection.
- Once the above step is successful, click on Activate SSO. Please note that this step is important for SSO enablement.
- Optionally, enable the check box to send emails to notify all users of the SSO enablement, else click Enable.
Notes:
- For any user to utilize Clumio login through Azure SSO, the user needs to be explicitly added in the Clumio UI; Administration > Access management > Users and should be assigned to the Clumio SAML Application created in Azure Directory.
- If there are two SAML signing certificate's present under the SAML Certificates section when editing SAML configurations, delete the certificate that is no longer needed, as there is a known issue with MSFT where the metadata URL/XML file may potentially reference the undesirable certificate.
Contact [email protected] with any questions or concerns.
Updated 2 months ago